
If there is anything the tech world has learned about security, its that four-digit PINs are fundamentally unsafe. Align that against a poorly managed security foundation, and what you have is an open invitation for brute-force attacks. Unfortunately, this is what Apple has done with their iCloud implementation. If an Apple computer is remotely locked by an iOS device, the user would need to enter a 4-digit PIN on the Find My Mac app in order to unlock the machine.
A Github user by the name of knoy has uploaded iCloudHacker: its only about 70 or so lines of Arduino code that doesn't just make it ridiculously straightforward to brute-force your way through the Find My Mac lockout, but it also dances around the surprisingly lackluster security controls that Apple had tried to implement. The coder reports that it has been successfully tried and tested on 2010 & 2012 13" MacBooks.
The code in this program isn't doing anything fancy or special, nor is it exploiting something behind the scenes. It merely simulates a mouse and keyboard via USB and proceeds to enter passwords similar to how any normal user would. Don't get comfortable however-- this is worse than if it was utilizing some obscure exploit. What this means is that the same method can be repeated with anyone just entering passwords over and over again, and more importantly, it means they're being allowed to do so without the OS preventing them.
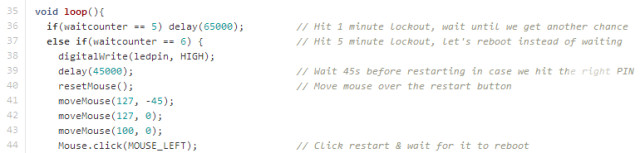
Rather than waiting for the 5 minute lock-out to expire before having another attempt, its quicker to just reboot
The first thing the program does upon boot is wait 5 seconds for the WiFi pop-up, and it would then move the mouse cursor over to the pop-up and close it. It then starts looping through the possible PIN combinations until it eventually hits a one minute security lockout, which makes the user wait before being able to guess again. At this point the program would, just like a normal user, wait for one minute before continuing the process. Again, it eventually hits another security lockout-- this time for five minutes. Rather than wasting time and waiting, the program simply moves the mouse cursor over to the restart button, restarts the computer, and does everything all over again. Rebooting results in the computer starting from a completely clean state as if the brute-forcing just a moment ago had never taken place.
The coder suggests that the maximum time it would take to brute-force any machine would be 60 hours. When its finally done, it starts flashing the LED's to tell the user that it has successfully brute-forced its way in.
This implementation however is fairly simple and doesn't account for the many years of research put into combination theory and analysis. For example, if we look to the research undertaken by Datagenetics, we learn some very startling facts about 4-digit pins:
- 26.83% of all 4-digit PINs account for only 20 combinations.
- The most popular PIN number is 1234 which accounts for 10% of all combinations, which means that 10% of all machines could be cracked in a single guess
- 20% of PINs are just 5 combinations, meaning that 20% of machines could be cracked in just 5 guesses.
- 50% can be cracked in 426 guesses.
- Repeated-pair couplets of numbers in a format such as XYXY (ie 1212, 2323, 5454, 0808) account for 17.8% of all observed pin numbers.
The code can be easily modified to account for the above and more, and there are hundreds if not thousands of text files out in the wild which have already listed 4-digit PINs in order of likeliness.
When looking at this issue we have to keep in mind that what is happening here is in fact significant, no matter how insignificant or time consuming it might appear. The significance isn't in the type of attack itself, or what the attack does, but in that there is a false sense of security for users regarding their Apple MacBooks and desktop computers.
So how can this be fixed? Easy. Among others, the first improvements that come to mind are:
- Increase the minimum number of digits to six. An increase to just five digits increases the number of possible combinations ten times, and an increase to six digits increases the number of possible combinations by 100 times.
- Require the use of symbols and letters, with the ability for both lower and uppercase letters
- Introduce persistent records of previous unsuccessful attempts
- Require MacBook-initiated two factor validation
Although this method isn't new or revolutionary, it comes at a very bad time for Apple, as just over a week ago there was a disastrous vulnerability in iOS and OSX regarding SSL, which was followed with a discovery of an iOS vulnerability that allowed full background monitoring.
Source: Github















41 Comments - Add comment