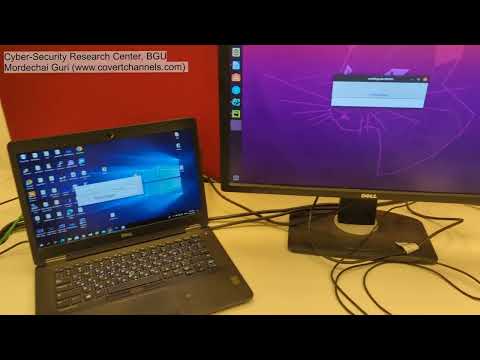
Security researchers at the Department of Software and Information Systems Engineering, Ben-Gurion University of the Negev, Israel, have discovered a new cyber-attack technique that they have named “SATAn”.
If you have guessed from the name that perhaps the new technique has something to with the SATA storage interface, then you would be right. The new SATAn method is basically a way to steal information and data from air-gapped systems by using the SATA cables as a wireless antenna to transmit data and information from a compromised PC on to a receiver somewhere close.

For those unaware, air-gapped systems are basically devices that are lonely entities, as they are not part of any network. The study has found that around the 6 GHz frequency band is where the transmission via SATA cables is the most effective.
Here"s how the security researches at the Gurion University of the Negev describe their findings about SATAn:
Although air-gap computers have no wireless connectivity, we show that attackers can use the SATA cable as a wireless antenna to transfer radio signals at the 6 GHz frequency band. The Serial ATA (SATA) is a bus interface widely used in modern computers and connects the host bus to mass storage devices such as hard disk drives, optical drives, and solid-state drives. The prevalence of the SATA interface makes this attack highly available to attackers in a wide range of computer systems and IT environments.
[...]
Our experiments show that the SATA 3.0 cables emit electromagnetic emissions in various frequency bands; 1 GHz, 2.5 GHz, 3.9 GHz, and +6 GHz. However, the most significant correlation with the data transmission spans from 5.9995 GHz to 5.9996 GHz. The idea behind the covert channel is to use the SATA cable as an antenna and control the electromagnetic emission.
[..] The results show that attackers can use the SATA cable to transfer a brief amount of sensitive information from highly secured, air-gap computers wirelessly to a nearby receiver.
Additional testing has shown that reading operations on SATA are more effective in producing stronger signals than writes. This also makes the overall attack situation easier, as writing can often require more privileges.
The results show that read operations yield a signal with an average of 3 dB stronger than write operations.
Notably, read operations may require lower permissions than write operations. For example, an application may be permitted to read data or configuration files but might be restricted in writing to them.
As expected, an active SATA or disk activity means lower effectiveness for SATAn. This means an attacker would ideally want to avoid someone like a Chia miner.
The above results indicate that the attack can be a maintained event (sic) with active workloads on the system, which are CPU and I/O bound. However, the covert channel is rendered less effective when intensive disk activity is involved due to the reduced quality
Finally, the attack can also be carried out on virtual machines, though the effectiveness is significantly reduced:
The results show an average reduction of 5 dB in the signal quality in VM compared to the signal generated from the host.
The video below demonstrates such an attack:
You can find the full details on SATAn at this link. (PDF)