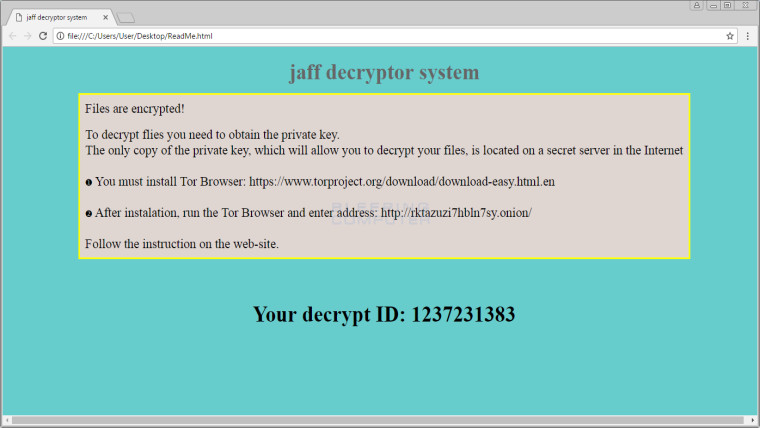
A new strain of ransomware has recently been discovered, which employs old tactics by cybercriminals, but still takes advantage of the rapid rise of the value of Bitcoin.
Dubbed "Jaff", the malware was detected by MalwareHunterTeam. It was found to be distributed via the Necurs botnet, which is an infamous distributor of malware like Locky, which it closely resembles. Like many ransomware, it employs the classic technique of sending spam emails that are designed to look important to the receiver.
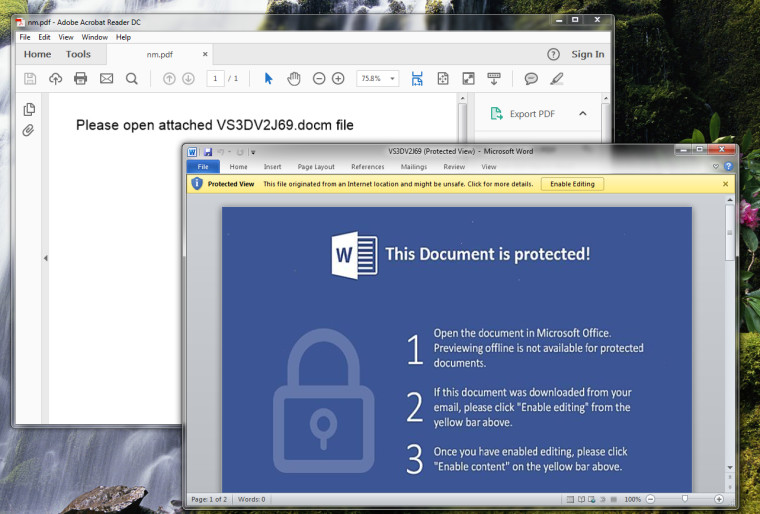
A PDF file will be downloaded, which will subsequently open a .docm Word file. At this point, the document will ask the receiver to click "Enable Content" to reveal the message. However, doing so will start the file's dirty work.
According to BleepingComputer, it will begin to gather information about the user, and then execute a number of files. Moreover, once the Jaff installer is executed, this will start the encryption process, which will lock a large number of files, appending ".jaff" to all of them, preventing proper access.
Once this process is done, a lock screen will be displayed, asking victims to go to a Tor website to find out how they can decrypt their files. The ransomware is demanding for 2 bitcoins, which is currently equal to roughly $3,600.
Unfortunately, in an analysis conducted by Fabian Wosar of Emsisoft, there is no known way of decrypting infected files without paying a ransom.
Many ransomware variants are known to exploit Word/Excel macros, as cybercriminals can easily make receivers believe that a sensitive document has been sent to them, making it easy to enable the content and launch the doom within.
Despite this, this ransomware is a good reminder to be careful of our activities on the internet, as cybercriminals are now getting more creative to trap victims, aiming to drain them of their hard-earned money.
Source: BleepingComputer

















14 Comments - Add comment