
A banking Trojan for Android dubbed "Svpeng" recently saw an update, according to Kaspersky Lab, gaining functionality like a keylogger, and ability to exploit the operating system's accessibility features to steal data.
Distributed through malicious websites that offer fake Adobe Flash software, it was further discovered that the malware also affects fully updated versions of Android.
Once installed, it checks if the device's language is set in Russian. If not, the program requests to use accessibility services, which will subsequently grant it administrator rights and make it the default SMS app on the device.
At this point, the Trojan can send and read text messages, make calls, and read contacts. To make matters worse, it can block any attempts to remove its rights as an administrator, as well as being able to access the UI of other installed apps and steal data from them. Svpeng also takes screenshots every time the user pushes a button on the keyboard, which are then uploaded to a Command & Control (C&C) server.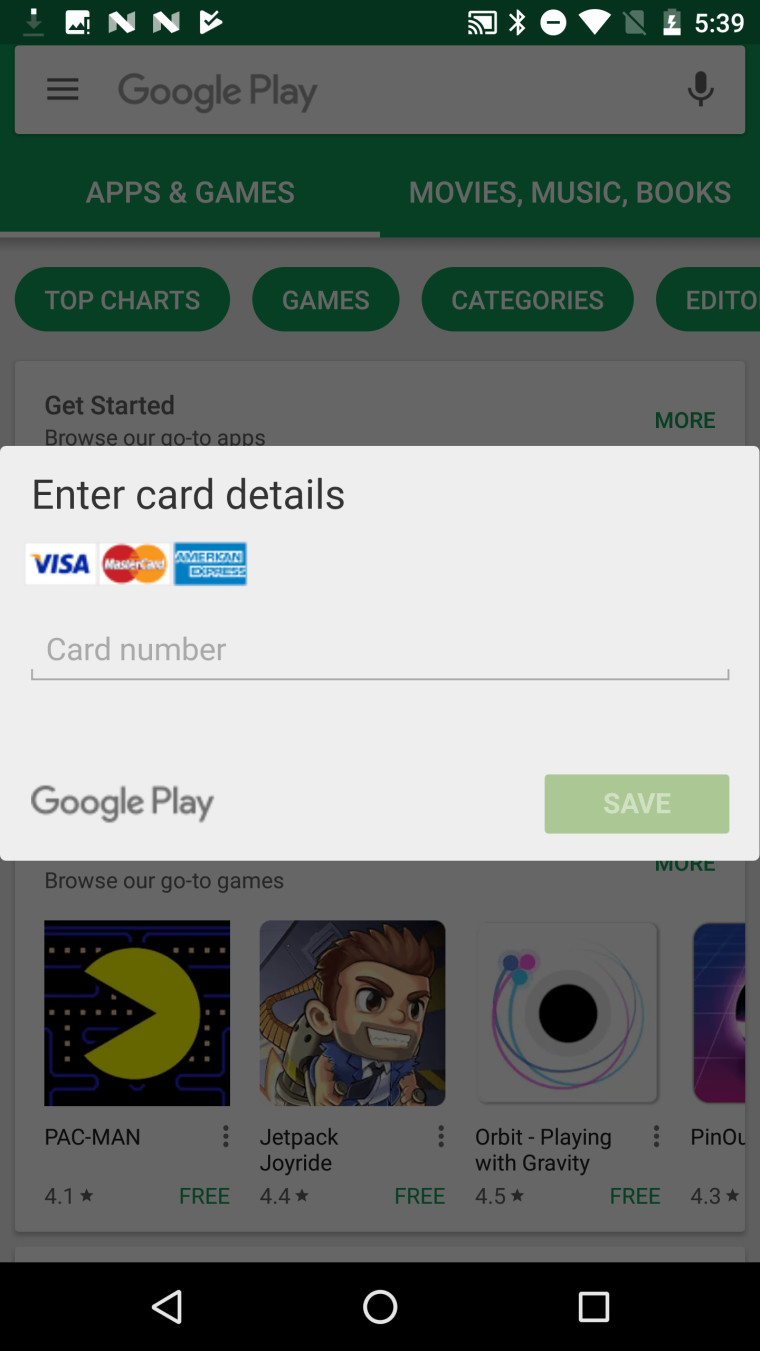
It does not end there, however; the Trojan can also identify what banking app is being used by the user, and then display a phishing link, in the hopes that the victim will enter their real banking credentials (pictured). This runs the risk of personal and financial theft.
Fortunately, Kaspersky found that there have only been a small number of Svpeng attacks, although these were recorded in 23 countries. Russia was affected the most, but it must be noted that the malware doesn't attack devices that are in the Russian language. "This is a standard tactic for Russian cybercriminals looking to evade detection and arrest," wrote Roman Unuchek, senior malware analyst at Kaspersky Lab.
All things considered, it pays to be careful of the websites we visit on our mobile devices, as well as the programs we download. It is not recommended to install apps from outside of official stores, as they are very likely to contain malware, thus putting ouronline security at risk.
Source: Kaspersky Lab via ZDNet| Screenshot via Kaspersky Lab


















15 Comments - Add comment