
An Android threat campaign using fraudulent reading and education apps to infect devices with a Trojan horse and steal Facebook credentials has recently been discovered.
According to a report by cybersecurity firm Zimperium, the campaign has been active since 2018 and primarily targeting Vietnamese readers. The Trojan, which they named "Schoolyard Bully," has been found in various applications that were downloaded from the Google Play Store and third-party app stores.
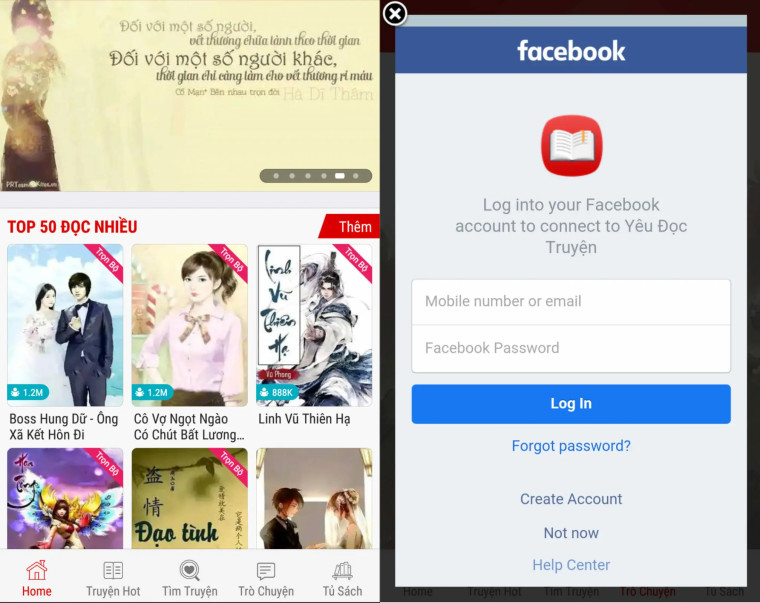
These apps pretend to be educational applications with a wide range of books and topics for users to allegedly read. However, the apps' true goal is to steal information, such as:
- Name on Facebook profile
- Facebook ID
- Facebook email/phone number
- Facebook password
- Device name
- Device API
- Device RAM
The Trojan steals these data by opening a legitimate Facebook login page inside the app and injecting malicious JavaScript code to obtain the user inputs. The malware can even evade antivirus programs and machine learning virus detections.
According to Zimperium, the threat campaign has victimized at least 300,000 users across 71 countries. However, the exact number of countries could be underreported because the applications are still being found in third-party app stores.
Zimperium pointed out the significant effect of the campaign:
Facebook reaches nearly 2.96 billion monthly users and continues to be the number one social media platform. As attackers leverage the Schoolyard Bully Trojan to gain unauthorized access to credentials, they have far more success accessing financial accounts. Nearly 64% of individuals use the same password that was exposed in a previous breach. With the percentage of users recycling passwords, it is no surprise the Schoolyard Bully Trojan has been active for years.
To protect your device from potentially malicious applications, always check an app's reviews. Make sure as well that your antivirus software is updated. Finally, carefully assess the permissions requested by apps. If an app is asking for a permission that is irrelevant to the program's function, it could be malicious.
Source: Zimperium

















1 Comment - Add comment