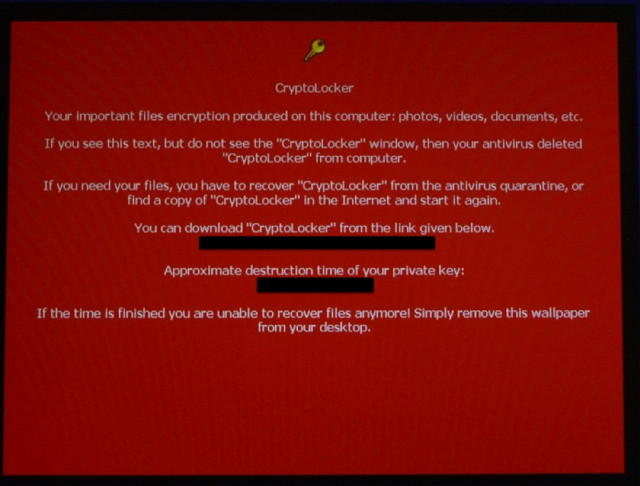
2013 saw the introduction of an extremely annoying piece of ransomware called CryptoLocker that was fairly original in its implementation. Ransomware would typically lock a victim's computer, demanding that they pay a fee in order to unlock the machine, however CryptoLocker was different.
CryptoLocker would encrypt the files on the victim's storage using AES-256 bit encryption and demand about $300 in bitcoin in order to retrieve the decryption key. If the victim didn't pay within a specified time, then the victim's files would remain encrypted forever. Well, until a couple of days ago, at least.
Computer security experts and researchers from the firms Fox-IT and FireEye have collaborated to reverse engineer the CryptoLocker software in a project they called "Operation Tovar." The collaboration between the two has led to the identification of many of the private keys used by CryptoLocker, and they have subsequently developed a free decryption assistance website and tool to help victims of the ransomware retrieve their data at no cost.

The site requires the user to upload any file that has been affected by the ransomware (they specify that they will not store or view the file), and the tool will email the user the relevant private key that can be used for decryption. At that point the user must download a specific tool, enter the private key and the location of the encrypted file, and the tool will decrypt the encrypted file.
Although the software unlocks the original CryptoLocker malware, the researchers at FireEye point out that there are deviations and copycats of CryptoLocker that they would not be able to unlock. One of these deviations has been recently discovered to infect Synology NAS devices, however there is no indication of whether or not this decryption tool would be able to help victims of the new deviation. Unfortunately, the only avenue available for victims of the ransomware would be to pay the ransom or suffer having their files permanently encrypted.
The decryption assistance website can be accessed here.
Source: FireEye | Images via FireEye
















20 Comments - Add comment