
Wi-Fi networks are no strangers to vulnerabilities, and now, a team at the cybersecurity firm ESET has discovered a security vulnerability that potentially affects over a billion Wi-Fi enabled devices (via ZDNet). Particularly, devices employing Broadcom and Cypress Wi-Fi that use WPA2-Personal or WPA2-Enterprise WiFi security protocols, with AES-CCMP encryption seem to be affected.
The security vulnerability stems from a variant of the WPA2 (KRACK), which previously affected Amazon Echoes and Kindles. Dubbed as Kr00k, the flaw allows malicious hackers to sniff, intercept and decrypt some type of WiFi network traffic that relies on WPA2 connections.
The vulnerability is enabled during the process of dissociation (disconnection due to weak Wi-Fi signals) where a unique key that encrypts data packets over the Wi-Fi network gets reset to an all-zero value. ESET claims that malicious hackers can put devices in a prolonged state of dissociation and use Kr00k to intercept and decrypt packets using the all-zero key.
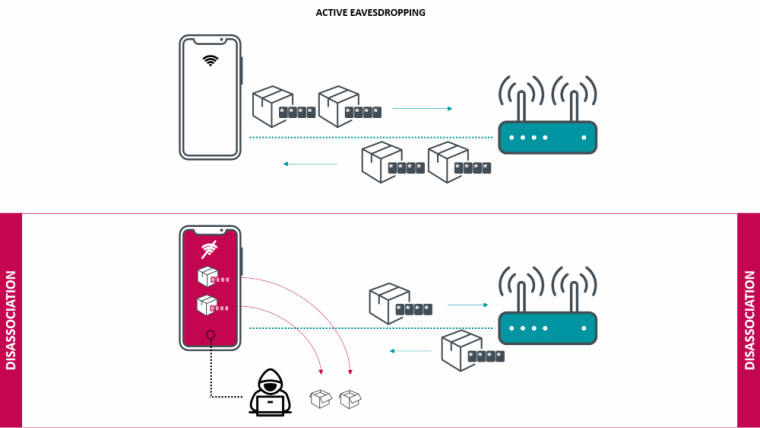
The team at ESET confirmed that Kr00k impacts devices like including Apple's iPhone, iPad, and MacBook. Amazon Echo and Kindle are also listed. So are Samsung Galaxy devices and access points from Asus and Huawei, among others.
The good news is that ESET has already been at work with Broadcom, Cypress, and other relevant companies to curb the issue. Security updates fixing the flaw should already be instated by now, as corroborated by ESET:
According to some vendor publications and our own (non-comprehensive) tests, devices should have received patches for the vulnerability by the time of publication. Depending on the device type, this might only mean ensuring the latest OS or software updates are installed (Android, Apple and Windows devices; some IoT devices), but may require a firmware update (access points, routers and some IoT devices).
If you want to ensure that your device has been patched against Kr00k, you may check your Wi-Fi device's OS firmware changelogs for fixes against CVE-2019-15126, which is the unique ID assigned to track this bug. Moreover, since Kr00k affects WPA2 connections, using the newer WPA3 WiFi authentication protocol should ensure safety against this vulnerability.
All in all, if you are interested in finding out more, you may refer to ESET's research paper on Kr00k here.














