It seems some cybercriminals are channeling their inner Star Trek fanboy, as a new ransomware variant named after a character from the popular science fiction media franchise has recently been discovered.
Detected by Avast malware researcher Jakub Kroustek, the "Kirk" ransomware is written in Python. While it is not currently known how it is distributed, the ransomware is noted to be masquerading as an application called Low Orbital Ion Cannon, a network stress testing application. Once executed, Kirk will generate an AES password which will be used to encrypt a victim's files. This will subsequently be encrypted by an embedded RSA-4096 encryption key.
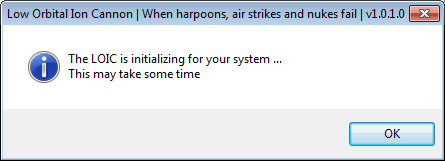
Next, a prompt will display stating "The LOIC is initializing for your system ... This may take some time." At this point, the Kirk ransomware is silently encrypting files. The malware reportedly affects 625 file types, including widely used ones like .mp3, .docx, .zip, .jpeg, and .wma, among many others. A ransom note will be dropped soon after this process is done.
Typical ransomware would usually ask for Bitcoins or MoneyPak as payment in order to unlock the files. However, the Kirk ransomware asks victims to pay in Monero, another secure crypto-currency like Bitcoin. For the first two days, it will ask for 50 Monero, which is equal to roughly $1265. It will double every few days, and if no payment is made by the 31st day, the decryption key gets permanently deleted, according to the ransom note.
Of course, with the ransomware being named after a Star Trek character, the cybercrooks went all the way and named the malware's decryptor "Spock." The criminals promise to send the software to the victim once the Monero payment has been made. As of the moment, there is no known way to decrypt files that have been affected by the Kirk ransomware for free.
There are still no known cases of anyone being affected by this ransomware. However, it still pays to be careful of our activities on the internet, to be able to lessen the chances of contracting such malware in the future.
Source: Jakub Kroustek via BleepingComputer

















15 Comments - Add comment